We are often asked this question and the companies often wonder: Can we legally and securely retain credit card numbers? The answer is yes—but only under strict conditions defined by the Payment Card Industry Data Security Standard (PCI DSS) version 4.0, specifically Requirement 3.5.1.
Let’s break down what this requirement means and how your company can stay compliant while handling sensitive cardholder data.
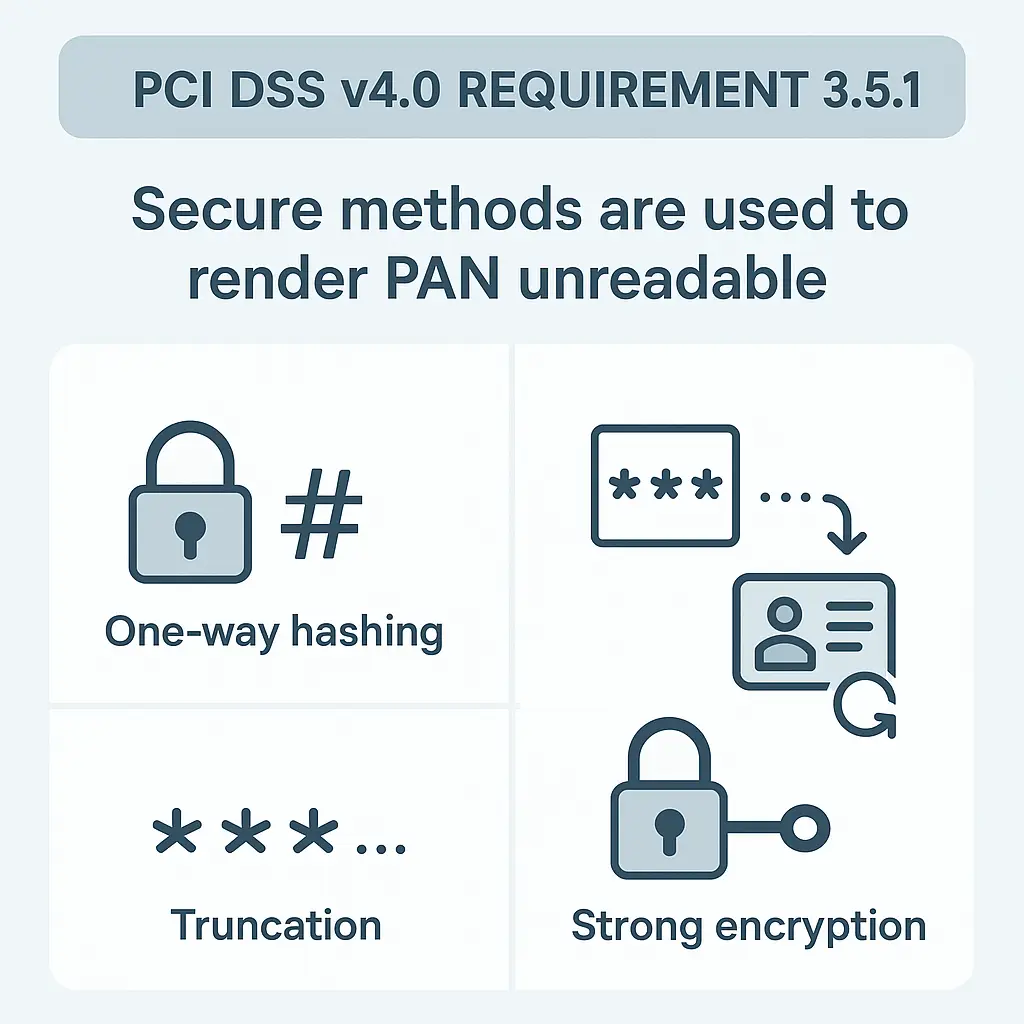
Requirement 3.5.1 mandates that Primary Account Numbers (PANs) must be rendered unreadable wherever they are stored. This is a critical security measure to protect cardholder data from unauthorized access and breaches.
One-Way Hashing
Truncation
Index Tokens
Strong Encryption
Yes, but only if:
Failing to comply with Requirement 3.5.1 can result in:
Retaining credit card numbers is possible—but it’s a responsibility that demands rigorous security practices. PCI DSS v4.0 Requirement 3.5.1 provides a clear framework for how PANs must be protected. If your company chooses to store this data, ensure full compliance to safeguard your customers and your reputation.
Call us anytime or email us for your compliance requirements cheers
.

If your business processes credit or debit card payments, PCI

Navigating Your PCI DSS Audit: A No-Nonsense Guide for Aussie

PCI DSS QSA audit Australia — In today’s digital economy,